Executive Summary
This report documents a security assessment performed on a controlled, authorized wireless environment. The purpose of the exercise was to evaluate the strength of a WPA2-PSK (Wi-Fi Protected Access II – Pre-Shared Key) network configuration and to analyze its susceptibility to password-based attacks.
Key Findings:
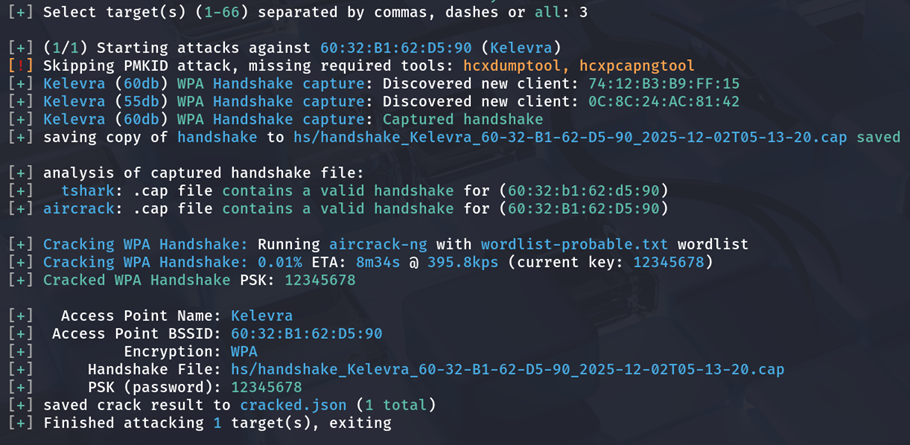
The pre-shared key (12345678) of SSID Kelevra was successfully recovered in approximately 8 minutes using a small built-in wordlist in Wifite.
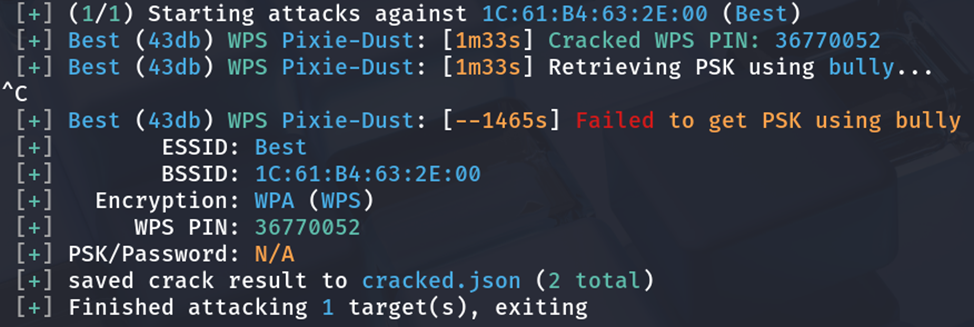
The pre-shared key (36770052) of SSID Best was successfully recovered in approximately 2 minutes using offline Pixie-Dust attack. No handshake or wordlist was needed.
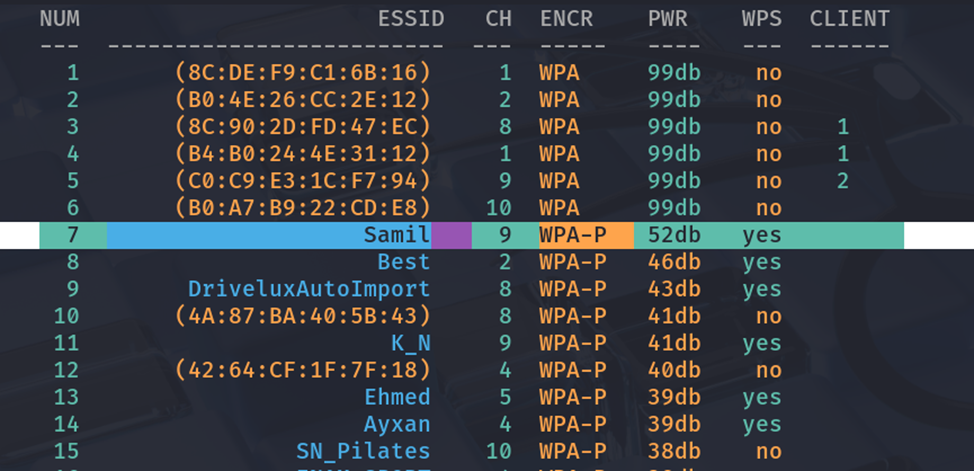
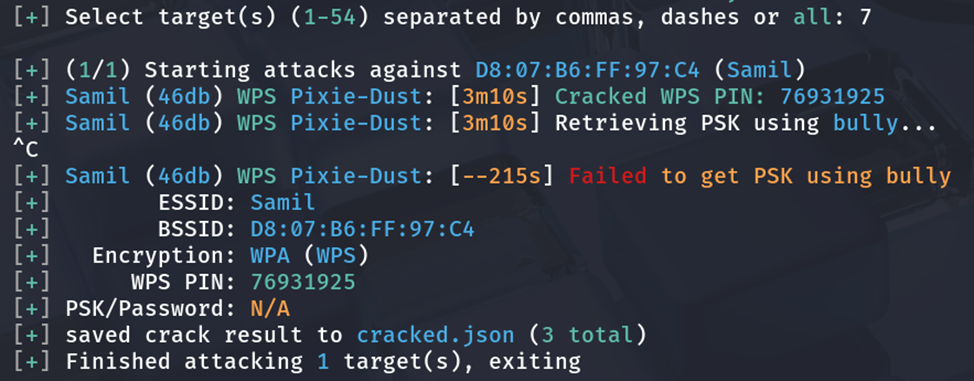
The pre-shared key (76931925) of SSID Samil was successfully recovered in approximately 3 minutes using offline Pixie-Dust attack. No handshake or wordlist was needed.
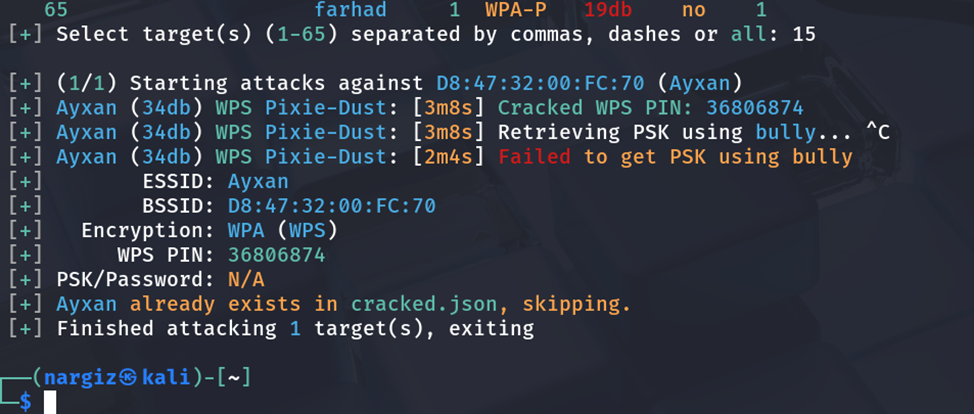
The pre-shared key (36806874) of SSID Ayxan was successfully recovered in approximately 3 minutes using offline Pixie-Dust attack. No handshake or wordlist was needed. This exercise clearly shows why short numeric-only passphrases (including default router PINs) must never be used in production environments.


Scope
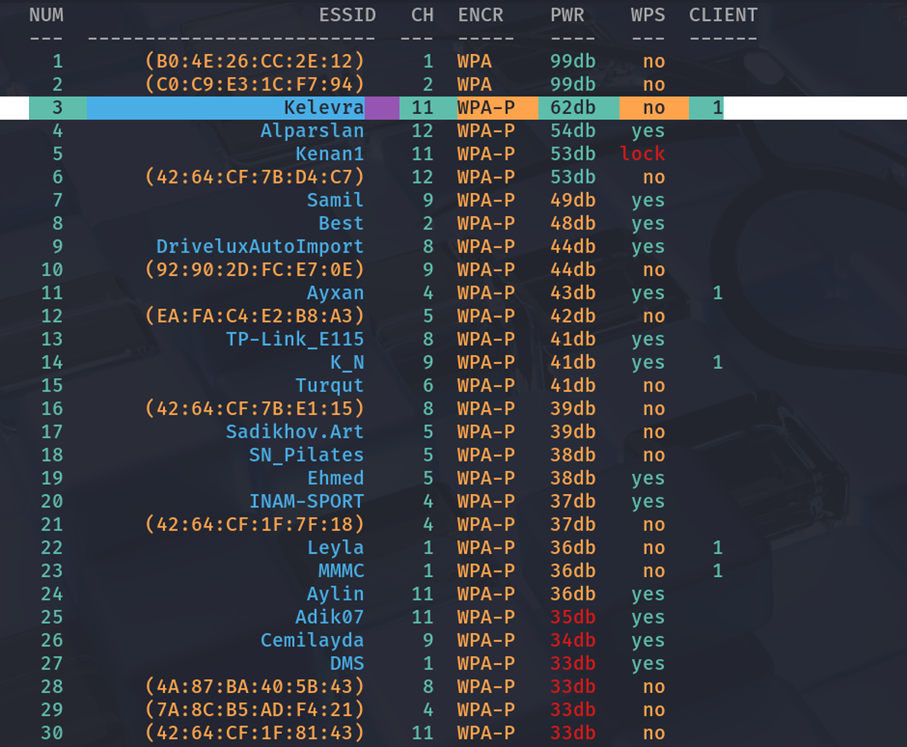
- Target 1: SSID Kelevra (2.4Ghz)
- MAC 1: 60:32:B1:62:D5:90
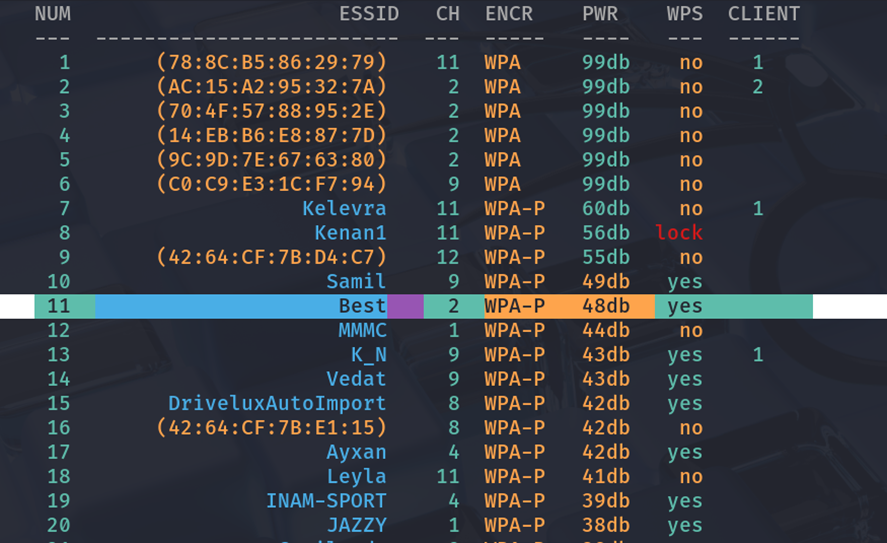
- Target 2: SSID Best (2.4Ghz)
- MAC 2: 1C:61:B4:63:2E:00
- Target 3: SSID Samil (2.4Ghz)
- MAC 3: D8:07:B6:FF:97:C4
- Target 4: SSID Ayxan (2.4Ghz)
- MAC 4: D8:47:32:00:FC:70
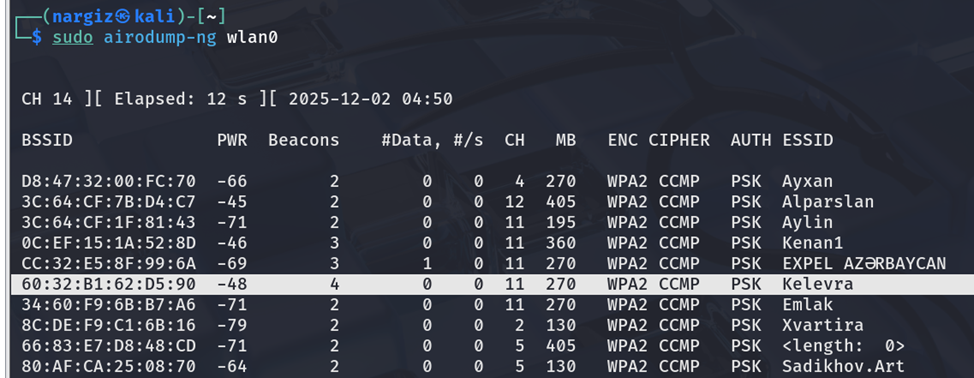
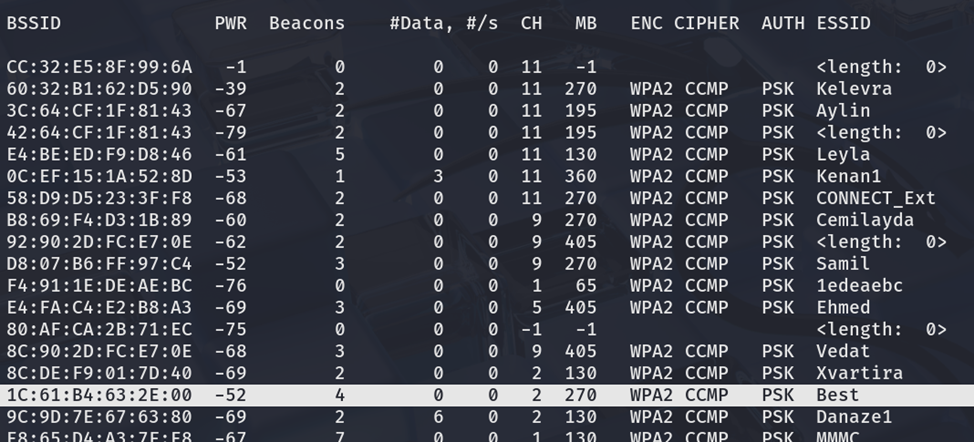
Methodology
- System preparation
- Installed Wifite2 tool from the official GitHub repository
- Verified Wireless Interface
- Launched Targeted Attack to WPA Networks
- Choosing Target
- Wifite2 scan detected 60+ networks; target #3 (Kelevra) was manually selected
- Automatic monitor mode activation
- Clean WPA handshake captured in 8 minute 34 seconds on Target 1; 1 minute 33 seconds on Target 2; 3 minute 10 seconds on Target 3, 3 minute 8 seconds on Target 4
- Dictionary attack launched with built-in probable-wordlists; Pixie_Dust attack
- Passphrases: 12345678, 36770052 and 76931925,36806874 recovered instantly

- Key Findings
- Finding 1: 8-digit numeric-only PSK (12345678) in use
- Severity: Critical
- Time to crack: 8m34s
- Finding 2: WPS enabled + chipset vulnerable to Pixie-Dust
- Severity: Critical
- Time to crack: 1m33s
- Finding 3: WPS enabled + chipset vulnerable to Pixie-Dust
- Severity: Critical
- Time to crack: 3m10s
- Finding 4: WPS enabled + chipset vulnerable to Pixie-Dust
- Severity: Critical
- Time to crack: 3m8s
- Recommendations
- Use minimum 14–16 random characters (upper + lower + numbers + symbols)
- Immediately disable WPS on all routers
- Migrate to WPA3-Personal whenever possible
- Never use default or numeric-only PINs/passphrases
- Buy routers that are not vulnerable to Pixie-Dust/Reaver
Conclusion
The evaluation demonstrated that the tested WPA2-PSK network was vulnerable due to the use of a weak and predictable password.
The password was recovered quickly through offline testing, highlighting the importance of strong passphrase selection in WPA2 security models.
By applying the recommendations in this report, the wireless network’s resistance to attacks can be significantly strengthened.

